Table of Contents
In today's digital age, cybersecurity threats are more prevalent than ever, and among the most disruptive are Distributed Denial of Service (DDoS) attacks.
These attacks can cripple websites, disrupt services, and cause significant financial and reputational damage. In this article, we will explore what a DDoS attack is, how it works, and what steps you can take to protect your online assets.
What is a DDoS Attack?
1. Definition:
- A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic.
2. Key Characteristics:
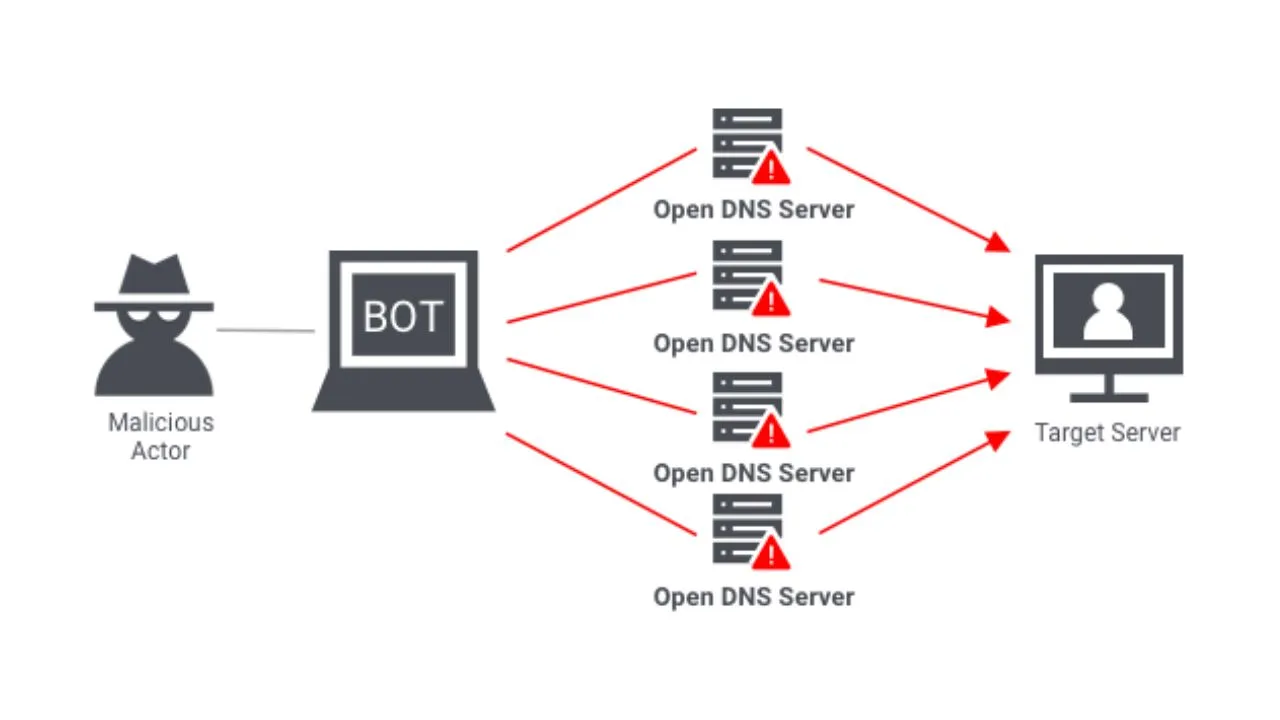
- Distributed: Unlike a traditional Denial of Service (DoS) attack, which typically uses a single source, a DDoS attack originates from multiple compromised devices, often spread across various locations.
- Denial of Service: The primary goal is to deny legitimate users access to a service by exhausting the target's resources.
How Do DDoS Attacks Work?
1. Botnets:
- Creation of Botnets: Attackers create a network of infected devices, known as a botnet, by spreading malware that turns these devices into "zombies" under their control.
- Command and Control: The attacker uses command and control (C&C) servers to coordinate and manage the botnet, directing the infected devices to simultaneously send a flood of requests to the target.
2. Types of DDoS Attacks:
- Volume-Based Attacks: These attacks aim to consume the bandwidth of the target, often measured in bits per second (bps). Common methods include UDP floods and ICMP floods.
- Protocol Attacks: These focus on exhausting server resources or intermediary communication devices such as firewalls and load balancers. Examples include SYN floods and Ping of Death.
- Application Layer Attacks: These target specific applications or services, aiming to exhaust resources at the application layer, often measured in requests per second (rps). HTTP floods are a typical example.
3. Attack Execution:
- Launching the Attack: The attacker instructs the botnet to begin sending a high volume of traffic to the target.
- Overwhelming the Target: The flood of traffic overwhelms the target’s resources, causing slowdowns or complete service outages.
- Sustaining the Attack: DDoS attacks can be sustained over long periods, making mitigation challenging and potentially causing prolonged disruptions.
Why are DDoS Attacks Dangerous?
1. Service Disruption:
- DDoS attacks can render websites, applications, and services unavailable, impacting users and causing significant downtime.
2. Financial Loss:
- Extended downtime can lead to lost revenue, especially for e-commerce sites and businesses that rely on online services.
3. Reputational Damage:
- Frequent or prolonged attacks can damage a company's reputation, eroding customer trust and leading to long-term business impacts.
4. Collateral Damage:
- DDoS attacks can also affect network infrastructure, leading to broader disruptions beyond the immediate target.
How to Protect Against DDoS Attacks
1. Implement Traffic Filtering:
- Use firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) to filter out malicious traffic before it reaches your servers.
2. Leverage CDN and Load Balancers:
- Content Delivery Networks (CDNs) and load balancers distribute traffic across multiple servers, making it harder for a DDoS attack to overwhelm a single server.
3. Enable Rate Limiting:
- Rate limiting controls the number of requests a user can make in a given timeframe, mitigating the impact of application layer attacks.
4. Deploy DDoS Mitigation Services:
- Utilize specialized DDoS mitigation services that detect and mitigate attacks in real time, ensuring continuous service availability.
5. Prepare an Incident Response Plan:
- Develop and regularly update an incident response plan to quickly and effectively respond to DDoS attacks when they occur.
Conclusion
Understanding DDoS attacks and how they work is crucial for safeguarding your online presence. These attacks can cause significant disruption, financial loss, and reputational damage.
By implementing robust security measures and staying vigilant, you can protect your website and services from the devastating effects of DDoS attacks.
Stay Secure with Our Expert DDoS Protection Services!
Don't let DDoS attacks disrupt your business. Softhat IT Solutions offers comprehensive DDoS protection services to keep your website and services secure. Contact us today to learn how we can help you defend against DDoS attacks and ensure uninterrupted service.
